You Deserve Stronger Security
Accelerate your cloud strategy with security consulting solutions that strengthen your defenses, improve compliance, and elevate operational performance.

Discover Risks, Strengthen Security
See what’s exposed—and fix it fast. Our security assessment reveals hidden risks and delivers a prioritized plan to keep your organization secure
Know Your Risk, Defend What Matters?
Our cybersecurity assessments expose hidden threats and prioritize critical gaps giving you a structured path to stronger defenses.

Why Clients Trust Us?
Proven Methodology That Accelerates Maturity
Our Discover → Identify → Secure approach cuts risk by up to 40% and builds a scalable, long-term security foundation.
Security Leadership You Can Trust
24+ years of expertise guiding enterprises toward stronger, risk-
reduced security.
Security Highlights — How We Add Value
- Identify Vulnerabilities with 90% Accuracy
- Enhance Security Posture by 60% in 3 Months
- Achieve Compliance with 100% Standards
- Reduce Security Risks by 75%

Our Approach
We help organizations strengthen their security posture through a comprehensive, end-to-end security assessment that focuses on identifying gaps, reducing risk, and aligning technology controls with business priorities.
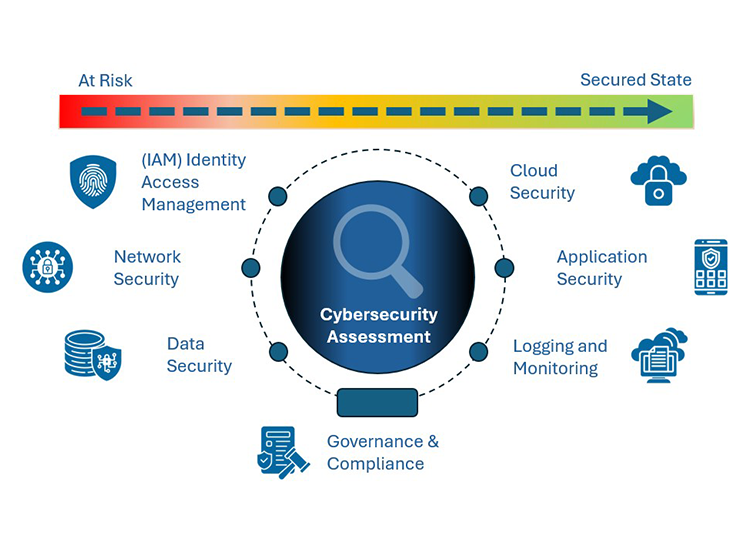
Our assessments span seven critical domains that form the foundation of a secure, resilient, and compliant enterprise environment
DISCOVER
We assess your cloud and security environment to understand your current posture.This gives clarity on strengths, gaps, and improvement areas.
IDENTIFY
We pinpoint vulnerabilities, misconfigurations, and compliance gaps across cloud, identity, network, and applications.
SECURE
We design and implement security strategies including cloud architecture, IAM, monitoring, and XDR-driven defenses.
GET IN TOUCH
Start The Conversation With Free 10-Minute Consultation
Let’s discuss strategy, services, and solutions. Or any other high- priority technology and compliance concerns.
We look forward to learning about your organisation, sharing our
process, and providing value, early and often. We’re here to help.

Our Expertise
Areas of focus during our Comprehensive
Security Assessment
Strategic technologies that enhance our cloud capabilities and strengthen your protection.

Identity Access Management
We ensure identities are created, governed, and secured so users always have the right access with Zero Trust controls.

Data Security
We protect sensitive data through strong classification, encryption, and governance to reduce compliance and breach risks.

Network Security
We strengthen your network with secure design, segmentation, and monitoring to reduce attack surface and improve resilience.
